Step 1-2: Connect Your Data to Ayfie
Connect to all your data silos, including the Windows environment and other systems and apps.
Connect to all your data silos, including the Windows environment and other systems and apps.
Extract personal information from your documents with advanced NLP techniques.
Locate where sensitive data lives, even within screenshots or images.
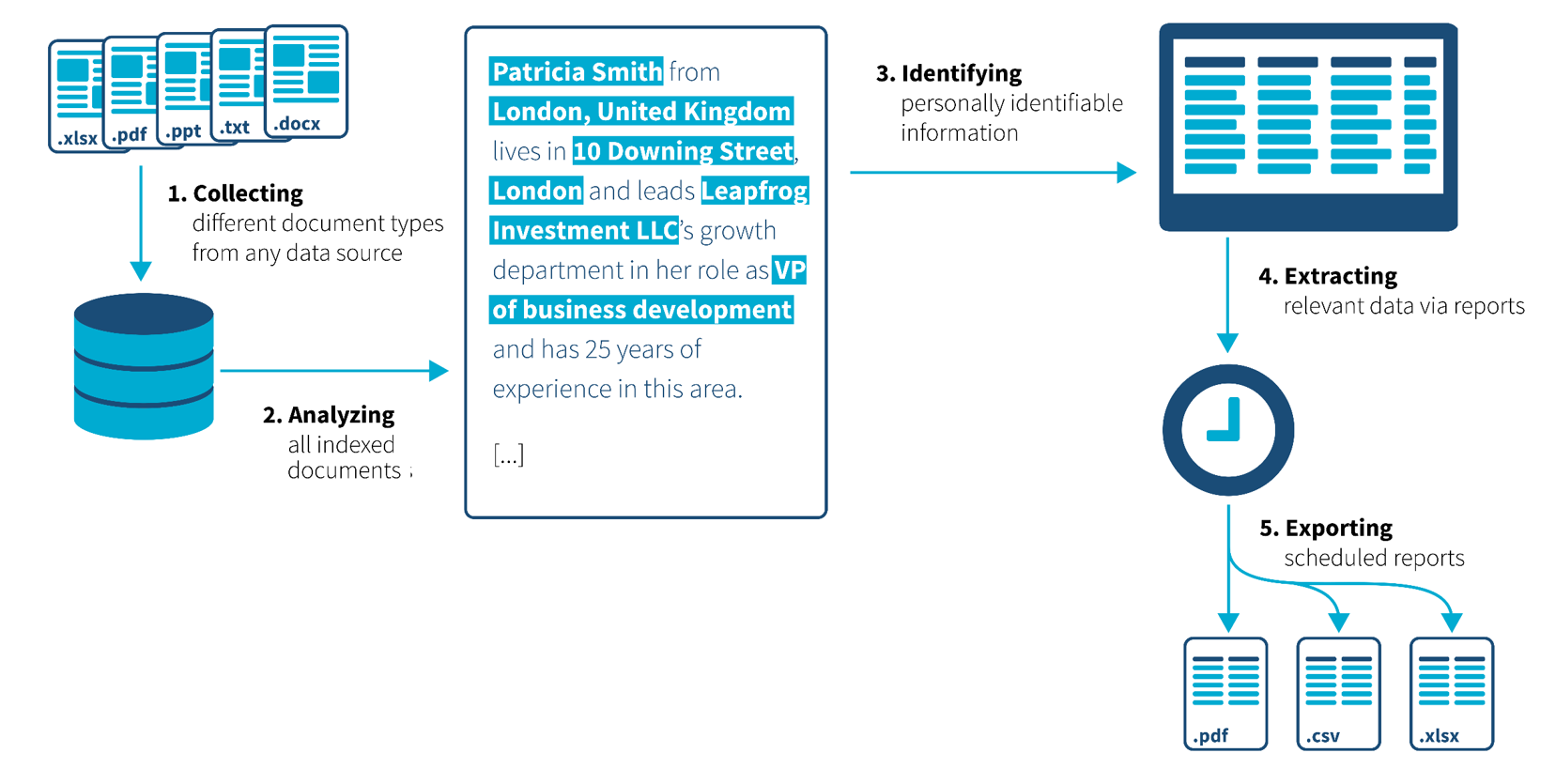

Review large amounts of information fast using functionalities such as Annotations, Tags and Timeline in Ayfie Locator.
-1.png?width=85&name=Frame%20(5)-1.png)
With Ayfie you can be certain to know all the details as well as finding what your case might be missing of important details.
.png?width=84&name=Frame%20(6).png)
Thanks to having all you need in one single platform you are more efficient in your job, as well as being able to collaborate across teams.
In the event of a personal data breach, data controllers must notify the appropriate supervisory authority without undue delay and, if possible, no later than 72 hours after becoming aware of it (Article 33 of the GDPR).
The GDPR sets fines of up to $24 million or 4% of the total worldwide turnover of the preceding financial year - whichever is higher - for infringements.
Based on a recent study conducted by IBM the average cost of a data breach is $3.9M. Main cost contributors are detection and escalation, notification, post data breach response and lost business cost.
USE CASES
Several of our existing clients using the Ayfie Platform and having connected their core systems want stay compliant and be ready. With Supervisor it's a fast and easy step in the right direction.
We have users ranging from Head of Compliance, Privacy Officers, Data Protection Officers or in a dual role where GDPR is one area of responsibility. Being able to answer to employee, client or board requests are at the very center of why they choose Supervisor.
Taking Privacy and Compliance seriously, in the context of the GDPR or because most businesses today handle and process personal and sensitive data, is as important as their very existence. Therefore being compliant, is being responsible as a company.
Have a look at the video below and see for yourself in 3 simple steps on how to be create and run a report in the case of a Data Breach, in our GDPR & Compliance Tool Supervisor.
.png?width=492&name=Rectangle%20141%20(1).png)
Every company stores personal data. A Data Subject Access Request (DSAR) is a request from a data subject, e.g. a former employee, to be provided with a copy of the personal data being processed by a data controller and an explanation of the purposes for which the stored personal data is being used.
The GDPR imposes exorbitant fines if required reports can not be produced within days. However, in an age of exponentially growing data volumes, diverse information silos, and a wide variety of data protection models, it is becoming increasingly difficult to meet the legal requirements.
Whether you are a customer, consumer or employee, you have the right to see what data companies have stored about you. When you make a request to access all this data, it is called submitting a DSAR, or a Data Subject Access Request.
Creating a DSAR usually involves a lot of work for a Compliance Officer, DPO, privacy representative etc. That's why you need a tool that both simplifies and streamlines your hectic and complex tasks at hand.
When a data breach occurs, you have 72 hours to react.
Employees, customers, suppliers, prospects – every company stores personal data about individuals. Should this data fall into the wrong hands, e.g. through a hacker attack, every affected individual has to be informed by legal requirement.
Since the introduction of the GDPR, companies have been fined if required reports are not available for affected people within a short time. Worst case scenario, the effort required for reporting on that data can even be business-threatening.
With exponentially growing data volumes, numerous cloud providers, and a wide variety of data protection models, it is becoming increasingly difficult to meet these legal requirements without software solutions.
.png?width=492&name=Rectangle%20141%20(1).png)
.png?width=492&name=Rectangle%20141%20(1).png)
Have you ever heard the expression “buried under paperwork”? That is exactly how M&A teams feel at the beginning of any litigation or Due Diligence exercise.
We understand that starting a process like that can be demotivating because you know it will take time and that you will have to be both strategic and detail-oriented. Read how you can cut down the time needed to sift through documents but also maintain the attention for detail required with these processes.
For all Data Subject Access Requests, risk analysis, compliance audits, data breaches, and data leakages, we need to take actions that often consist in deleting non-compliant sensitive data or moving it to more secure places. This is referred to as data deletion.
Data deletion has a lot to do with your internal workflows. Do you have proficient processes for data deletion? Is it possible you could be missing a folder or a file in the process?
With Ayfie Supervisor we help making the process of data deletion comprehensive, exhaustive, secure and verifiable.
.png?width=492&name=Rectangle%20141%20(1).png)